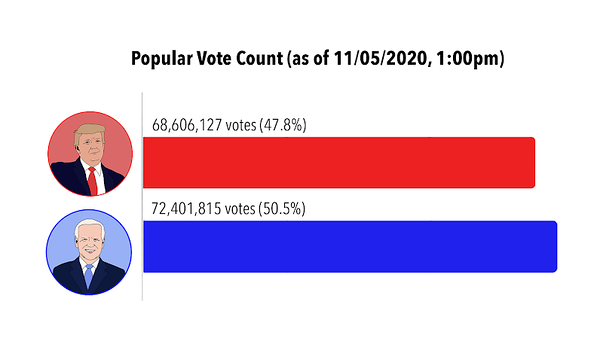
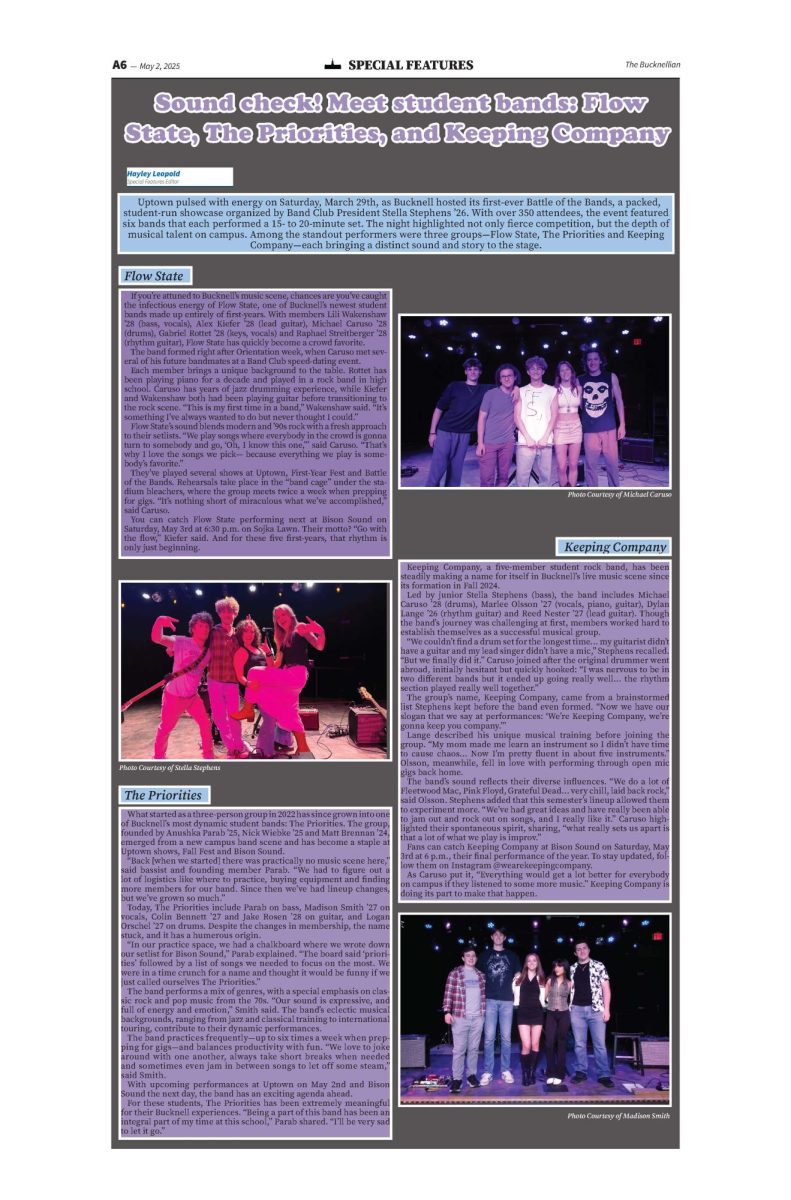
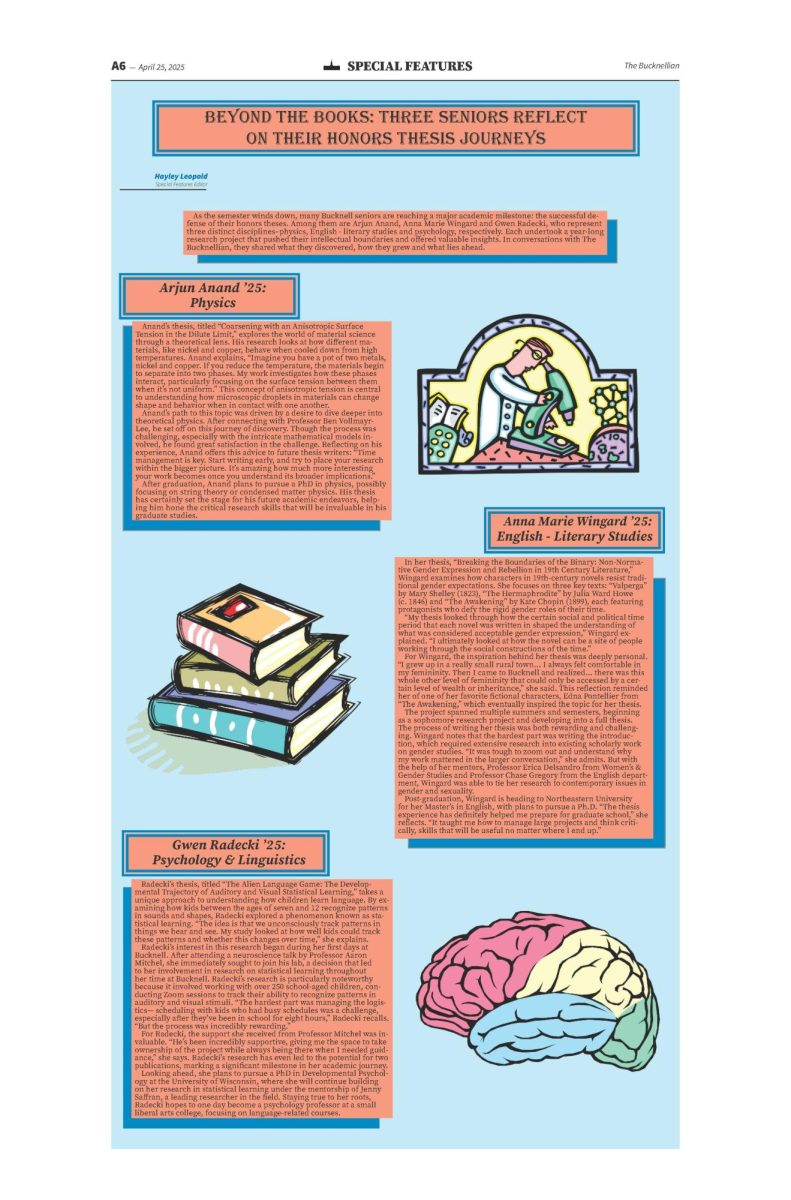
Cyber security threats: Just a click away
October 27, 2016
In the modern world, we back up every piece of personal information onto our phones and computers. Every daily function we perform can now be done on an electronic device, which is convenient but dangerous from a security perspective. With apps like Venmo and Apple Pay, so much of our financial information is just a click away. We register and transfer personal information on our devices without realizing that hacking and breaches of security are much more common than we think. These issues are very prevalent on campus—so much so that the University recently hired Chief Information Security Officer Chris Bernard to help keep students and faculty safe. In light of National Cyber Security Awareness Month, we are delving into current security problems and how to combat them.
Common cyber security problems
In order to prevent cyber security breaches, it’s important to understand which problems are most common. According to Bernard, the two most common cyber security issues among college students are phishing and malware. Phishing is when an attacker attempts to gain personal information, usually through email, whereas malware is software that gets downloaded from dangerous websites or phishing emails that can hijack your computer. Both of these breaches can be dangerous and should receive immediate attention.
“Anytime a student (or anyone for that matter) suspects a cyber security incident, their first call or stop should be the Bucknell Tech Desk who can evaluate the situation and engage other staff members within L&IT (Library & Information Technology) to help resolve the problem,” Bernard said.
How to avoid security problems
There are multiple precautions to take to avoid most cyber security issues. Bernard stressed that students need to be conscious of which websites and emails look hazardous. He provided three triggers to look out for that may indicate fraud. First, phishing emails often emphasize urgent needs (the suspension of a bank account, for example), threatening consequences if action isn’t immediately taken. Second, these emails may ask for a response including personal information like passwords or social security numbers. Third, the emails could provide a link that could gather personal information or install software that could slow down your computer or even lock it until you pay ransom to regain access to it. Bernard also mentioned the importance of keeping your computer’s antivirus program up-to-date.
Cyber security abroad
Many students will study abroad in the coming semesters, so it’s important to be aware of the changes in cyber security overseas. According to Bernard, a lot of daily applications and security features are restricted or banned in other countries, so standard safety outlets may not be available. In certain countries, information stored on electronic devices is valued even more, resulting in a higher risk of theft. Hackers may try to find this information stored on your computer, or intercept it from the Internet.
“Successful attempts could expose not only Bucknell data, but also your personal IDs and passwords, travel itineraries, and other information that could make you a vulnerable target,” Bernard said. Students are not permitted to access any University services like Bmail or myBucknell in sanctioned countries like Cuba, North Korea, or Syria.
What is our campus doing?
To combat cyber security problems on campus, Bernard and the L&IT team have worked to raise awareness and provide students and faculty with necessary information about hacking and security breaches. They held an informational forum early in the semester for faculty, a Spot and Phish event in the ELC a few weeks ago, and have continuously posted information on their L&IT blog and the Message Center. According to Bernard, these efforts have two goals. The first goal is to start the relevant conversation of cyber security, and the second is to get faculty and staff to begin considering “What do YOU have to lose?” Bernard also shared that they have some projects in the works to begin examining trends among the statistics of security breaches.